Can you match “hack-cess” as fast as attackers’ “white-hat” innovation’s weakest links?
The vulnerability acrobatics intensify across today’s OT spheres. Pace, connectivity, and convergence soar. So do risks and requirements to path progressive gaps. Cyber criminals catapult complexity, weaponizing IoT influx and cloud onramps before many counteract the crux. It’s the ultimate gauntlet – spiraling attack paths and half-decade CVEs amplified by integration’s decentralized access.
Yet NERC CIP’s adaptive shields transition to strike a resilience rhythm. Expanding to low-impact systems. Paying supply chain mindsets. Promoting joint security strides. Standards that entwine risk balance, future-proofed principles and collective controls distilled the essential agility needed for such slippery threats and access avenues.
Because threat progress never pauses, despite dizzying attack densities. The only option is perpetually preempting risks through more galvanized game plans between public and private oversight. Do you have the vision and verve to pivot security at such a pace? Let’s decode the NERC CIP innovations safeguarding grids despite technical complexities. The cyber resilience strategies securing critical infrastructure as transformations outstrip the best. How chronically creative configurations contain sprawling threats. And why proactive protections must partner progress milestones to master such mercurial environments.
Expanding Protections to Match an Evolving Landscape
Legacy NERC CIP versions concentrated narrowly on high-impact Bulk Electric System (BES) cyber assets. But as exploits utilize more sophisticated tools, the scope widens.
Key expansions include:
- Extending Controls to Low Impact BES Components
Previously standards focused entirely on high and medium impact assets that directly supported grid operations. However, threats now deliberately target seemingly innocuous systems to gain initial beachheads before pivoting to higher value domains. Hence the need for baseline protections on low impact equipment – routers, workstations, credential stores. While not directly BES components, these provide backdoor access requiring addressal.
- Covering New Attack Surfaces like Supply Chain Compromises
Sophisticated actors now compromise equipment well before operational deployments through techniques like:
- Hardware/software implants during production
- Counterfeit substitution in logistics transit
- Malicious updates to third-party software dependencies
By legislating security diligence across the entire system life cycle rather than just perimeter protections, NERC aims to mitigate blindspots that bypass traditional network defenses.
- Emphasizing Proactive Testing to Validate Control Efficacy
Expanding scope requires expanded vigilance to ensure standards match reality, not just regulations. Accentuating simulated threat testing evaluates how implementations withstand emulated attacks targeting infrastructure mimicking the expanded NERC environments. This facilitates fortifying defenses pre-incident.
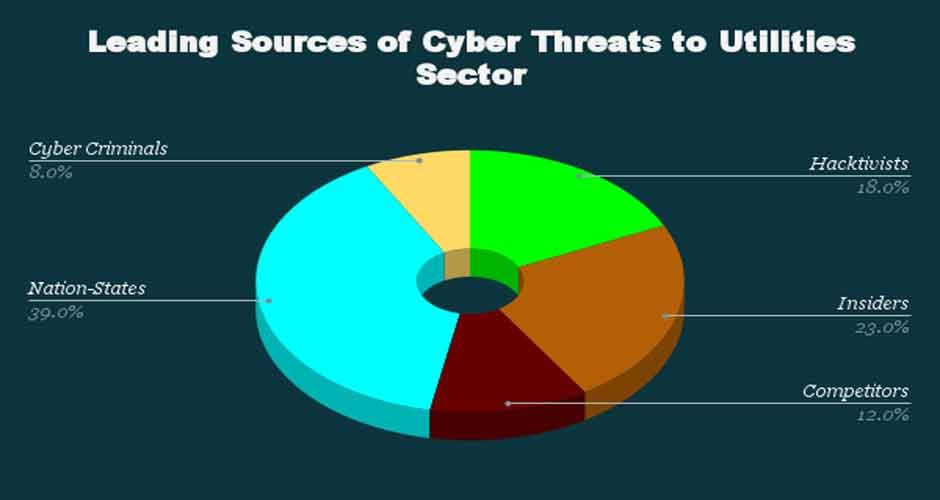
These innovations acknowledge that threats now originate both externally and internally, with actors ranging from nation-states to insiders. Controls must widen to account for these manifold risks. Supply chain compromises demonstrate one emerging vector, often inserting malware or hardware-level exploits. Hence standards adaptations to guard against such substitution or infiltration throughout the system lifecycle, rather than simply protecting perimeter access points.
“These standard innovations target several pressing risk areas, with priorities shifting to address new attack surfaces.”
Emerging Technologies Lead the Charge
While the tenets remain constant, the threat environment morphs rapidly. IoT, cloud migrations, converged networks now represent the most urgent focus areas as 90% of OT systems gain internet connectivity over coming years (Forrester).
Specific concerns involve:
- Securely configuring BES cloud implementations.
- Handling risks from increased OT/IT convergence.
- Managing connected devices and embedded controls.
- Adapting identity/access for new solutions.
Specifically, teams must now secure BES cloud configurations to avoid misconfigurations that could enable lateral access or exposure. Similarly, a more hands-on deck from IT/OT convergence mandates updated identity and access controls attuned to this cross-domain environment. Myriad sensors, smart devices, controllers also weave in, requiring specific IoT and embedded component protections against evolving telemetry and command injection-style risks.
“Adapting these dynamic environments requires balanced, flexible security models tailored to manage rapid change.”
Implementing Controls: Robust Yet Flexible
In such fluctuating environments, NERC CIP controls must walk the tightrope between security, reliability, and innovation. Microsegmentation limits exposure over 80% (ES-ISAC), allowing granular control without impeding operations.
Modern best practices move from blanket mandates towards more adaptive frameworks integrating risk analysis, data science, and surgical control precisions. This allows the rigor of security standards without hampering functionality improvements from new tech adoptions.
Specific techniques include:
- Risk-based policies over check-the-box mandates
- Data-driven analytics to contextualize and prioritize threats
- Security by design principles baked into new solution rollouts
“Innovative controls that are robust yet flexible enough for fluid technology shifts.”
Comparison of Legacy vs Modern Control Frameworks
| Legacy Approaches | Emerging Models | |
| Focus | Broad compliance | Risk-aligned security |
| Priorities | Static asset protection | Adaptive, analytics-driven |
| Implementation | Blanket controls | Tailored safeguard |
Proactive Postures through Collaboration
Entity-led exercises have increased 125% from 2016-2020 (NERC), enabling more proactive resilience. But realizing innovations requires:
- Industry collaboration to tackle problems collectively
- Threat emulationto continuously test defenses
- Metricsto measure efficacy of evolving controls
“More immersive testing and collective knowledge-sharing becomes critical during transitions.”
Balancing Progress With Protection
The stakes rise as infrastructure modernizes, with control system cyber incidents costing $1.5 trillion. But with adaptable frameworks, utilities can facilitate innovation while ensuring security and resilience.
Careful change management ensures protections evolve alongside new advantage-bearing technologies and integrations. Standards innovations must continue matching headlines of novel exploits. In this environment, resilience requires running as fast as threats multiply – evolving capabilities before catastrophic damages.
Conclusion
As innovation iterates our critical infrastructures, security must accelerate an equal magnitude. NERC CIP standards continue calibrating controls to counteract threats multiplying by minds faster than any individual defense. The themes remain unchanged – collectively harden systems, emulate emerging scenarios, integrate flexible measures, balance security and progress.
Yet the variables morph infinitely. Cloud habitats. Converged domains. Hyperconnected sensors and devices. With each new advantage also emerging attack paths to patch and perimeter less access to govern. By expanding standards scope, emphasizing risk balance, and promoting joint security sweeps, NERC CIP aims to share the load. To distribute capability-building across interdependent stakeholders so that together we out-frame threats in framing the future.
It’s a long road of resilience running faster than criminal creativity can sprint. But by formalizing collaboration channels, metrics for efficacy, proactive stress testing, and adaptive policy guides, NERC CIP helps swap secured innovation know-how. Can we collectively configure barricades robust enough for the most wicked vectors while allowing infrastructure progress to perpetuate? With shared vigilance, communicative controls and concentric commitment to pivot partnerships alongside threats – we stand the best chance of outrunning risks. For in unity and understanding, we each gain the vision of security possible.
Frequently Asked Questions
1. How can utilities match security velocity with tech advances?
Focus on risk-based models, cultivate vendor partnerships, and allocate resources to thoroughly test innovations pre-deployment.
2. What emerging skills should teams incorporate?
Prioritize cloud, IoT/OT, data analytics, ML, and automation security skills.
3. How can resilience increase given rising connectivity?
Maximize logging and monitoring for situational awareness. Utilize defense-in-depth, effective incident response, and advanced analytics.

















Comments